6 Browser-Based Attacks Security Teams Must Watch in 2025
Web browsers have become the central hub for modern work. From accessing cloud apps to managing business workflows, nearly everything employees do today runs through the browser. Unfortunately, attackers know this too — and they’re exploiting it.
This shift makes the browser one of the most important battlegrounds for security teams in 2025. Below, we’ll break down the most common browser-based attacks, how they work, and why they’re such a threat.
Why attackers target the browser
Attackers aren’t interested in your browser itself — their goal is the business data and applications behind it. Cloud apps, SaaS tools, and third-party services are now the backbone of modern IT, and therefore the prime target for compromise.
Instead of breaking into corporate networks, attackers increasingly go after users directly, exploiting the tools and services they access daily through their browser.
1. Phishing for credentials and sessions
Phishing is no longer just an email problem. Attackers deliver malicious links via text, chat apps, social platforms, ads, or even in-app messages. No matter the channel, the endgame is always the same: trick users into handing over credentials or session data in the browser.
Today’s phishing kits often bypass multi-factor authentication (MFA) by acting as a reverse proxy, stealing valid session tokens in real time. They also use advanced evasion techniques — from obfuscated code to fake CAPTCHAs — making detection harder than ever.
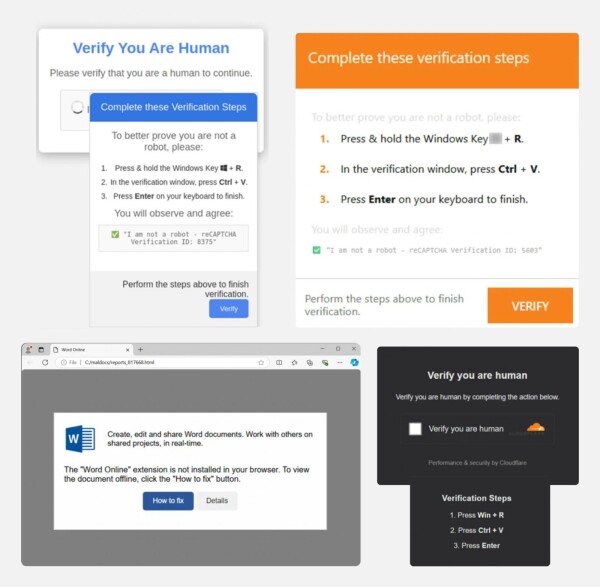
2. Malicious code delivery (ClickFix, FileFix, and variants)
“ClickFix” attacks trick users into copying and running malicious code under the guise of solving a browser challenge. Some variants target Windows (via Run, Terminal, or PowerShell), while others now hit macOS.
Originally known as “Fake CAPTCHA”, these attacks attempt to trick users into running malicious commands on their device — typically by solving some form of verification challenge in the browser.
These attacks often deliver info-stealing malware designed to capture browser sessions and credentials. The common thread? At some point, malicious code is silently copied from the browser to the device.
Variants such as "FileFix" have also emerged which instead uses the File Explorer Address Bar to execute OS commands, while recent examples have seen this attack branch out to Mac via the macOS terminal.
3. Malicious OAuth integrations
Instead of stealing passwords, attackers can bypass logins entirely by tricking users into granting permissions to a malicious OAuth app. Once approved, that app can access sensitive data and functions without needing to authenticate again.
This type of “consent phishing” sidesteps even strong MFA, since the login process itself is never challenged. With hundreds of SaaS apps in use, many outside of IT’s direct control, this attack vector is only growing.
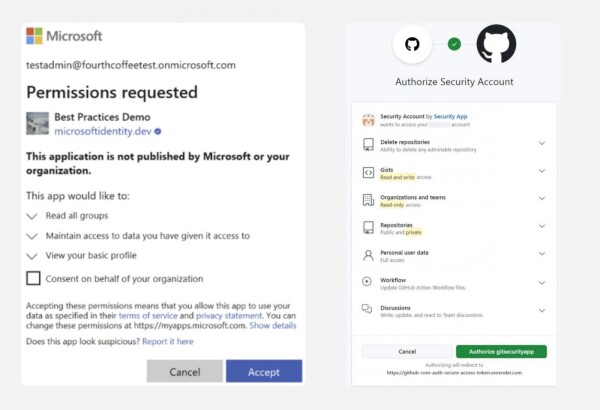
Consent phishing examples, where an attacker tricks the victim into authorizing an attacker-controlled app with risky permissions.
4. Malicious browser extensions
Extensions make browsers more powerful — but also more dangerous. Attackers can create their own malicious extensions or compromise existing ones, then use them to monitor activity, steal session cookies, or inject malware.
Because extensions can request powerful permissions (like reading all browsing data), even a single rogue extension can lead to major breaches.
The news around extension-based compromises has been on the rise since the "Cyberhaven extension" was hacked in December 2024, along with at least 35 other extensions. Since then, there has been regular reporting on data-stealing extensions impersonating legitimate brands, and impacting millions of users
5. Malicious file delivery
While email is still a common method for malware delivery, attackers now increasingly use drive-by downloads, advertising networks, and SaaS file-sharing to push dangerous files.
Some files contain self-contained phishing pages (such as HTA or SVG files) that open fake login portals in the browser. Others redirect users to malicious sites. The browser is the first place these downloads appear, making it a critical checkpoint for defense.
6. Stolen credentials and MFA gaps
Stolen passwords are still one of the simplest, most effective attack methods. If MFA isn’t enabled — or if shadow accounts (“ghost logins”) exist outside your main identity provider — attackers can use stolen credentials to walk right into business apps.
The browser provides visibility into real-world login behavior, showing where MFA is missing and which accounts are at risk.
Final thoughts
The browser has become the central attack surface for modern organizations. Phishing, malicious extensions, OAuth abuse, and credential theft all converge here, making it a high-value target for attackers.
For security teams, this means the browser is also the best place to gain visibility and stop these attacks before they escalate.